
IABs targeting SMBs
The digital threat ecosystem has become increasingly complex, with initial access brokers (IABs) emerging as a critical risk to small and midsized businesses (SMBs). These brokers exploit network vulnerabilities to sell access to the highest bidder, underscoring the urgent need for robust cybersecurity defense measures.
Despite the advancement and breadth of cybersecurity controls and software, we frequently observe IAB-based campaigns targeting SMBs due to a few main reasons. SMBs frequently operate with limited IT resources and cybersecurity expertise, which can lead to a lapse in their cybersecurity posture, making them easier targets for IABs. On top of this, SMBs play roles in larger supply chains, making them attractive targets for IABs seeking to compromise upstream and downstream business.
Understanding the IAB landscape
IABs are specialized cybercriminals who infiltrate networks not to launch direct attacks but to sell access to those networks to other malicious actors. This distinguishes them significantly from other threat groups that might exploit network vulnerabilities for immediate financial theft, espionage, or data destruction. IABs leverage a sophisticated array of techniques to remain undetected, making their activities particularly insidious. Their focus is on monetizing access rather than further compromise, making SMBs prime targets due to comparatively less sophisticated cybersecurity infrastructure than larger, enterprise-level corporations. The consequences of breaches orchestrated by IABs can be severe, leading to data theft, financial loss, and significant business disruption.
Recurring malware related to IABs
SocGholish
One prominent piece of malware that has been attributed to IABs and observed in numerous incidents is SocGholish. SocGholish, also known as FakeUpdates, is a form of malware that masquerades as legitimate software updates on compromised websites to deceive users into downloading it. This malware leverages web injections to deliver JavaScript payloads directly into browser memory. SocGholish infects victims through phishing emails containing links to compromised websites. Once a user clicks the link, the injected JavaScript will execute after the page is loaded by the user’s browser.
SocGholish techniques
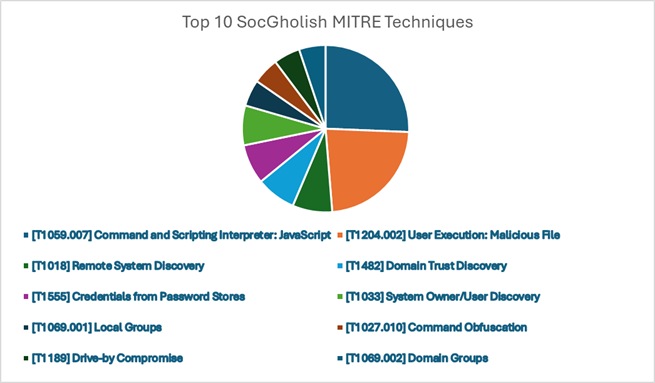
Initial infection
- [T1189] Drive-by Compromise
The most notable initial access technique from our data is Drive-by Compromise. In these instances, a user would encounter a webpage that would prompt them to update their browser. Upon clicking the prompt, a malicious file would be downloaded to the victim user’s device.
- [T1204.002] User Execution: Malicious File, [T1059.007] Command and Scripting Interpreter: JavaScript
The malicious file that the user would download in these instances was almost always a JavaScript file, infamously named “Update.js”. When the user downloads and executes the file, the local system binary Wscript.exe would then execute the .js file. The activity would appear like the command in the box below.
Wscript.exe [Path to Script File] Update.jsFigure 2: Typical SocGholish Wscript Execution
Post compromise
Our data suggests that most endpoint cybersecurity solutions would react to this suspicious activity, quarantining and terminating the malicious files and processes. However, in some cases, we have seen a variety of post-compromise techniques occur.
Discovery
- [T1018] Remote System Discovery, [T1033] System Owner/User Discovery, [T1069.002] Domain Groups, [T1482] Domain Trust Discovery, [T1069.001] Local Groups
Typical discovery techniques that threat actors will perform include enumerating various administrator groups, gathering information about the system that they have breached, and attempting to discover potential targets for deepening their hold and extending their folio of compromised assets.
net.exe localgroup AdministratorsFigure 3: Observed SocGholish discovery command
cmd.exe /c "systeminfo&net group "Domain Admins" /domain&net group "Enterprise Admins" /domain&net localgroup Administrators /domain&net localgroup Administrators"Figure 4: Observed SocGholish discovery command
- [T1555] Credentials from Password Stores
In the SocGholish campaigns, the primary post-compromise tactic observed involves using cmdkey.exe to extract credentials. This strategy likely serves dual purposes: to gain deeper access into the compromised system or network, or to potentially monetize the access by selling these credentials to other cybercriminals. These other adversaries may then engage in further nefarious activities, such as data theft or deploying ransomware.
cmd.exe /c "nltest /dclist:&nltest /domain_trusts&cmdkey /list" Figure 5: Observed SocGholish credential access
powershell cmdkey /list; nltest /domain_trusts; nltest /dclist:Figure 6: Observed SocGholish discovery command
Gootloader
Gootloader uses SEO poisoning to display compromised websites among search results, tricking users into downloading a malicious zip file containing a JavaScript file. This approach is often used to establish persistence and drop a Cobal Strike beacon for further covert activities.
Gootloader techniques
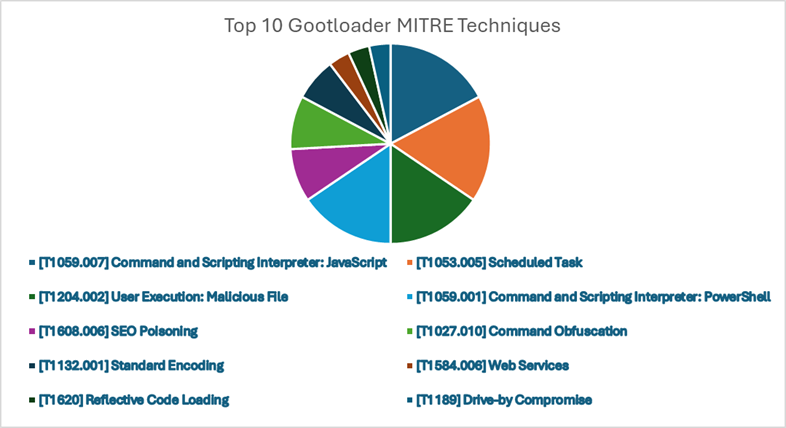
Resource Development
- [T1608.006] SEO Poisoning, [T1584.006] Web Services
Gootloader’s approach begins with hijacking web services to distribute malicious content. Following this, they manipulate search engine optimization tactics, ensuring these tampered sites appear more frequently for search terms that prospective targets might use. This strategy significantly increases the chances of individuals landing on these compromised pages.
Initial Infection
- [T1189] Drive-by Compromise
Much like SocGholish, Gootloader operators prey on vulnerabilities in web browsers or plugins to execute unauthorized code on a visitor’s system. Typically, a visitor will be redirected to a page that will automatically download a malicious JavaScript file.
- [T1204.002] User Execution: Malicious File, [T1059.007] Command and Scripting Interpreter: JavaScript
In most of our recorded incidents, once a visitor browses a web page compromised by Gootloader, a JavaScript file will be downloaded. This file will then be executed by either Wscript.exe or Cscript.exe.
Cscript.exe [Path to Script File] [File Name].jsFigure 8: Observed Gootloader Execution
Wscript.exe [Path to Script File] [File Name].jsFigure 9: Observed Gootloader Execution
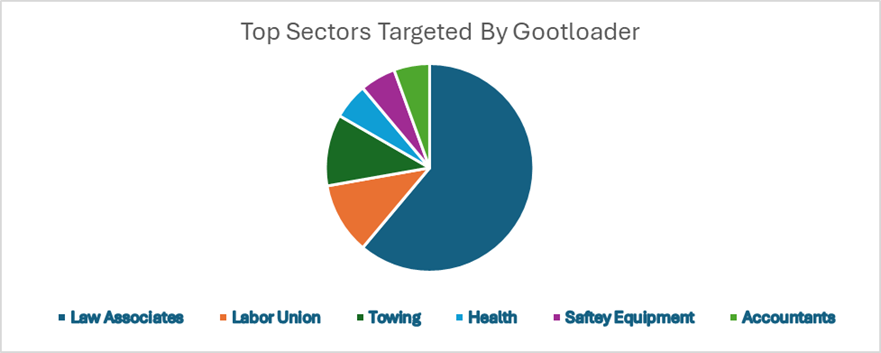
One interesting observation from our recorded incidents is the sectors targeted by Gootloader. A little over 60% of observed Gootloader incidents took place at businesses associated with law practices.
Common Trends
Among all the IAB-attributed malware that we have observed, there are some common trends that we can discern from their tactics, techniques, and procedures (TTPS).
Both groups use sophisticated social engineering tactics to deceive users into compromising their own systems, often through misleading prompts or search engine manipulation. Both employ techniques to evade detection, leveraging legitimate system tools and processes to carry out their operations discreetly. Additionally, they aim to establish initial access for further exploitation, whether for their own use or to sell as part of initial access broker operations, indicating a business model focused on monetizing access to compromised systems.
Implementing effective cybersecurity practices
To safeguard against IABs, SMBs must strive to maintain effective cybersecurity practices. This is inclusive of—but not limited to—establishing and implementing a comprehensive, layered approach to cybersecurity.
- Educating employees
Since human error can often lead to security breaches, it is critical to conduct regular cybersecurity training for all employees. Focusing on recognizing and responding to sophisticated phishing attempts and understanding the risk of visiting unknown websites, which are common entry points for IABs, is paramount to defending against these threats.
- Regular updating and patching systems
Ensuring that all externally facing services and systems are up to date with the latest cybersecurity patches can help deter IABs, as outdated and vulnerable systems are prime targets for their attacks.
- Implementing ample cybersecurity measures
Tools such as endpoint detection and response (EDR) systems, intrusion detection systems (IDS), and multi-factor authentication can help enhance an SMB’s cybersecurity posture. Implementing solutions that focus on behavior-based detections can thwart many IAB attacks, as they often leverage legitimate tools and system processes for malicious purposes.
- Conducting regular cybersecurity assessments
Regular cybersecurity assessments can help identify and rectify vulnerabilities within a network before they can be exploited by IABs. Regularly simulating IAB attack scenarios can help identify and strengthen any gaps in cybersecurity.
- Developing an incident response plan
A well-defined incident response plan can minimize the impact of a breach by ensuring a quick and organized response to cybersecurity incidents. Having detailed procedures for isolating compromised systems can help prevent IABs from gaining further access.
Conclusion
The threat posed by initial access brokers (IABs) and the malware used by them underscores a critical vulnerability in today’s cybersecurity landscape. These groups leverage deceptive social engineering tactics to initially compromise systems and then often sell access to the highest bidders—who may conduct even more destructive attacks.
This report highlights some technical details of these threats and the importance of SMBs adopting a proactive, multi-layered cybersecurity approach that emphasizes employee education, regular system updates and assessments, advanced detection technologies, and the establishment of a thorough incident response plan. As cyberthreats evolve, staying informed and prepared is paramount for safeguarding valuable data and maintaining business continuity.